iss vulnerability scanner
In 2010 Soroush Dalili and Ali Abbasnejad discovered the original bug GET request. The cybersecurity skill gap is.

12 Open Source Web Security Scanner Zum Auffinden Von Sicherheitslucken
A comprehensive scanner scans a wide range of devices and hosts on one or more networks identifying the device type and operating system and probing.

. Engagement Planning Preparation and Reporting. Penetration Testing It is highly recommended that Penetration Testing be conducted for UBC Systems containing or processing High or Very High Risk Information. Find fix vulnerabilities in your IDE with Snyk Code - efficient actionable code review.
The Nessus Vulnerability Scanner is one of the most common vulnerability scanners in the cybersecurity industry today. Regulatory requirements are changing. The latest version of scanner for IIS short file name 83 disclosure vulnerability by using the tilde character.
Microsoft IIS contains a flaw that may lead to an unauthorized information disclosure. In 2014 Soroush Dalili discovered that newer IIS installations are vulnerable with OPTIONS. For every vulnerability found in.
See Why Nessus Is 1 For Vulnerability Assessment - Start Your Free Trial Now. This was publicly disclosed in 2012. If all you need is a vulnerability scanner this is not your best bet.
Nessus Professional will help automate the vulnerability scanning process save time in your compliance cycles and allow you to engage your IT team. They have a wide array of scanners to chose from viz Internet Scanner for network based vulnerability assessment System Scanner for hosts Database Scanner Wireless Scanner for wireless LANs. This enables the tester to rapidly and quite exhaustively look for common configuration weaknesses in the targeted systems as well as for unpatched network server software.
Probably you guys can test them out. Scan data infrastructure for vulnerabilities to identify security risks such as missing patches weak passwords incorrectly configured privileges and default vendor accounts. Vulnerability statistics provide a quick overview for security vulnerabilities of this software.
Directories found http17216249128aspnet1 http17216249128secret1 Files. The intent is to manage security risks. Ad Snyks free code checker analyzes your code in real-time and provides fix advice.
The functionality that you get especially with the commercial version is total guarantee of value for your money. You can view versions of this product or security vulnerabilities. The network scanner requires at minimum MS SQLServer and ISS Site Protector to support it.
IIS Short Name Scanner v239. Vulnerability scanners work from a database of documented network service security defects exercising each defect on each available service of the target range of hosts. Wireshark is an advanced analysis tool with a packet sniffer that captures network traffic on local stores and networks to analyze data offline.
University IT Support Staff must not block UBCs Vulnerability Scanners. We review your IT environment and identify vulnerabilities associated with a range of IT assets including operating systems network devices databases and applications. Wireshark is a free and open-source network vulnerability scanner and empowers businesses to track activities at a micro level within the network.
Uncovering vulnerabilities in your attack surface. Secure ISS Vulnerability Assessment Process Scan. While it is also important to confirm your vulnerability hits by running other vulnerability scanners against your targets to eliminate the.
Buy a multi-year license and save. DESCRIPTION This standard establishes a common understanding of the roles and responsibilities for vulnerability scanning. Add Advanced Support for access to phone community and chat support 24 hours a day.
Site Home Quick Search. SATAN captured the attention of a broad technical audience appearing in PC Magazine and drawing threats from the United States Department of Justice. Security Administrator Tool for Analyzing Networks was a free software vulnerability scanner for analyzing networked computers.
ISS BlackICE PC Protection 36 cpj and cpu and possibly earlier versions allows local users to bypass the protection scheme by using the ZwDeleteFile API function to delete the critical filelocktxt file which stores information about protected files. The company offers a 7-day free trial of its profession edition which. The issue is triggered during the parsing of a request that contains a tilde character.
Click here PROTECTING YOUR CRITICAL ASSETS WITH MANAGED VULNERABILITY SCANNING Technology is advancing. MANAGED VULNERABILITY SCANNING WE REDUCE THE VULNERABILITIES WITHIN YOUR NETWORK TO PROTECT YOUR CRITICAL ASSETS AND STAY AHEAD OF CYBERATTACKS. Vulnerability scanning software relies on a database of known vulnerabilities and automated tests for them.
Proactively scanning government information systems allows security teams to identify potential exploits that can be mitigated. Ad Improved vulnerability detection with no false positives and faster results. FAENYSSCPA June 11 2002 Tom McDermott Cohn Consulting Group A division of JH.
Nessus Essentials formerly Nessus Home from Tenable allows you to scan up to 16 IP addresses at a time. To find a qualified penetration testing service contact informationsecurityubcca. Internet And Network Vulnerability Scanning With ISS.
Uncovering vulnerabilities in your attack surface. Nessus is the most comprehensive vulnerability scanner on the market today. A limited scanner will only address a single host or set of hosts running a single operating system platform.
Ad Among Security Scanning Tools Worldwide Nessus for Windows is 1 for Accuracy. The vulnerability is caused by a tilde character in a GET or OPTIONS request which could allow remote attackers to disclose 83 filenames short names. Ad Among Security Scanning Tools Worldwide Nessus for Windows is 1 for Accuracy.
It featured a web interface complete with forms to enter targets tables to display results and. Ad Snyks free code checker analyzes your code in real-time and provides fix advice. See Why Nessus Is 1 For Vulnerability Assessment - Start Your Free Trial Now.
Ad Improved vulnerability detection with no false positives and faster results. Planning for a Network Security Evaluation. Internet Scanner provides CVE related information in both the Common Policy Editor and the IS 70 Help file.
Simplify deployment in large-scale environments as multiple data sources database name type server IP ports and roles can be loaded and linked to assessments automatically. This includes directs web links to the CVE website. Find fix vulnerabilities in your IDE with Snyk Code - efficient actionable code review.
If all you need is a. Vulnerability scanning vendors once competed on how many vulnerabilities each product could discover. This page lists vulnerability statistics for all versions of ISS Internet Security Scanner.
Msf use auxiliaryscannerhttpiis_shortname_scanner msf auxiliaryiis_shortname_scanner set 17216249128 msf auxiliaryiis_shortname_scanner check 1721624912880 The target is vulnerable. Msf auxiliaryiis_shortname_scanner run Scanning in progress. Thereby securing government information systems from known vulnerabilities.

Vooki Web Application Vulnerability Scanner Hacking Books Hacking Tools For Android General Knowledge Facts

13 Online Free Tools To Scan Website Security Vulnerabilities Malware

Types Of Ciphers And How To Create A Cipher Order

Scan For Vulnerabilities On Any Website Using Nikto Tutorial Youtube
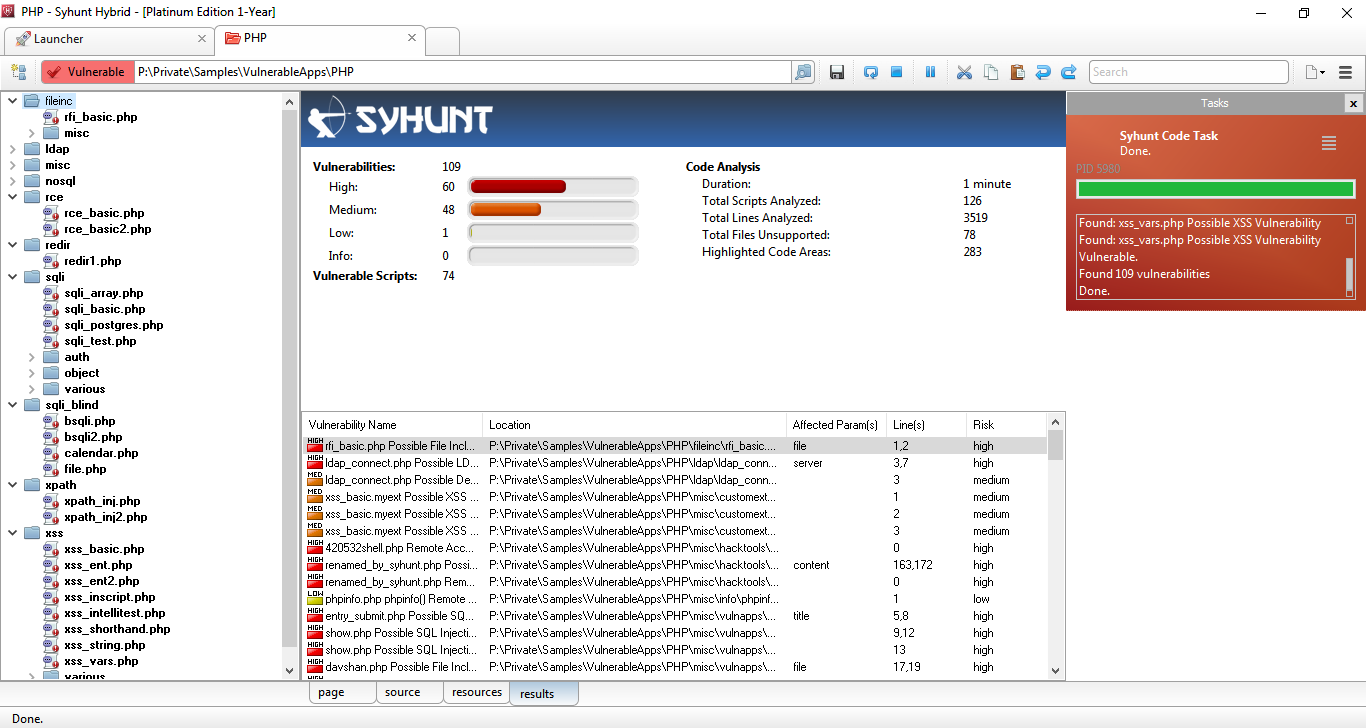
Source Code Analysis With Syhunt Code Vulnerability Scanner Tool

Katoolin Linux Mint Kali Linux Linux

Vulnerability Scanning Metasploit Unleashed

13 Online Free Tools To Scan Website Security Vulnerabilities Malware
Vulnerability Scanner For Web Servers N Stealth Security Scanner Blog Bujarra Com










0 Response to "iss vulnerability scanner"
Post a Comment